DoD Certificate Import – Admin Guide
This section is intended for system administrators who need to deploy Department of Defense (DoD) certificates across multiple devices or manage certificates in an organizational environment. These certificates are necessary to ensure secure access to DoD resources for all users.
Devices should be managed by a Mobile Device Management (MDM) system. The most secure and scalable way to deploy DoD certificates is by pushing a configuration profile (.mobileconfig file) containing the required device certificates to your fleet via MDM.
If your organization does not have an MDM solution, it is advised to have users follow the automated based installation instructions in the User Guide to ensure proper certificate deployment and trust settings.
You will find two approaches for installing and deploying DoD certificates with MDM:
-
Automated Script Method: Use an automated tool or script to generate a
.mobileconfigfile that includes all required DoD certificates. You can then upload this configuration profile into your MDM solution and push it to all managed devices. -
Manual Method: Download each required certificate, upload them individually into your MDM solution, and configure a certificate payload/profile. Then push the profile to your MDM-managed fleet.
Both methods achieve the same result—installing the necessary DoD certificates—but differ in terms of scalability and automation. Using a .mobileconfig profile with MDM is the preferred approach for organizations. If MDM is not available, users must have admin rights to install certificates, and manual steps may lead to errors or failed instructions.
This guide is designed for macOS Monterey and newer (typically the latest supported macOS versions). Older versions may require additional software or different steps. If you need a guide for an older version, please submit a request on GitHub Discussions.
Automated Script Method
This method uses a script or tool to generate a configuration profile (.mobileconfig) containing all required DoD certificates, which you then deploy via your MDM.
The automated script will:
- Download the latest DoD certificates directly from the official cyber.mil website.
- Generate a
.mobileconfigthat contains the latest DoD Certificates
Step 1: Download the script
Open Terminal and run the following commands to switch to your Downloads folder and download the script:
cd ~/Downloads
curl -O https://raw.githubusercontent.com/cocopuff2u/MacOS_GOV_Scripts/main/Keychain_And_Certificates_Scripts/Generate_DoD_Certs_Mobileconfig.py
The script file will now be saved in your Downloads folder as Generate_DoD_Certs_Mobileconfig.py.
Alternatively, you can download the script directly from GitHub using your browser: Download Generate_DoD_Certs_Mobileconfig.py from GitHub
Step 2: Run the script
Navigate to the folder where you downloaded the script (by default, your Downloads folder):
cd ~/Downloads
Then run the script with the following command:
sudo python3 Generate_DoD_Certs_Mobileconfig.py
If you kept the Terminal window open from the previous step, you can simply run the command above.
This will generate a DoD_Certificates_VX.XX.mobileconfig file in the same location as the script.
Anytime you run any scripts, it is recommended to review the code beforehand to verify it is not doing anything outside the described steps. You can inspect this one here
Example of a generated .mobileconfig file:
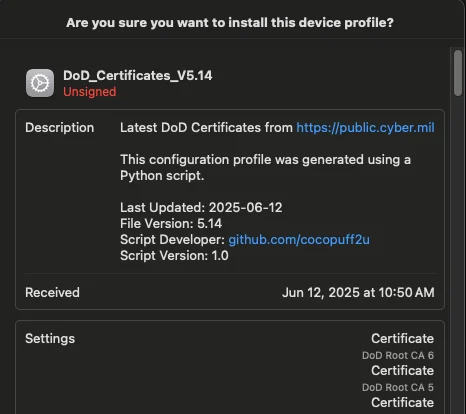
The information in the description is automatically generated by the script:
- File version: The version of the DoD certificates ZIP file downloaded from
cyber.mil. - Script version: The version of the script used to generate the profile.
- Last updated: The date the script was last run and the profile was generated.
Step 3: Upload the .mobileconfig to Your MDM
- Log in to your MDM admin console.
- Create a new configuration profile or certificate payload.
- Upload the generated
DoD_Certificates_VX.XX.mobileconfigfile.
Step 4: Assign and Deploy the Profile
- Assign the profile to the appropriate device groups or users.
- Push the profile to all managed devices.
Step 5: Verify Deployment
- On a managed device, open Keychain Access and check the System keychain for the imported DoD certificates.
- Confirm that certificates are present and trusted (no red X or warning icons).
- Test access to DoD resources to ensure functionality.
Manual Method
This method requires uploading each certificate file to your MDM and configuring a certificate payload to be deployed to all devices. The exact steps for uploading, assigning, and deploying certificates may vary depending on your MDM solution. The instructions below provide a general overview of the recommended process.
Step 1: Download DoD Certificates from an Authorized Location
- Go to cyber.mil.
- Or, you can download here (official link from cyber.mil) then skip to step 2
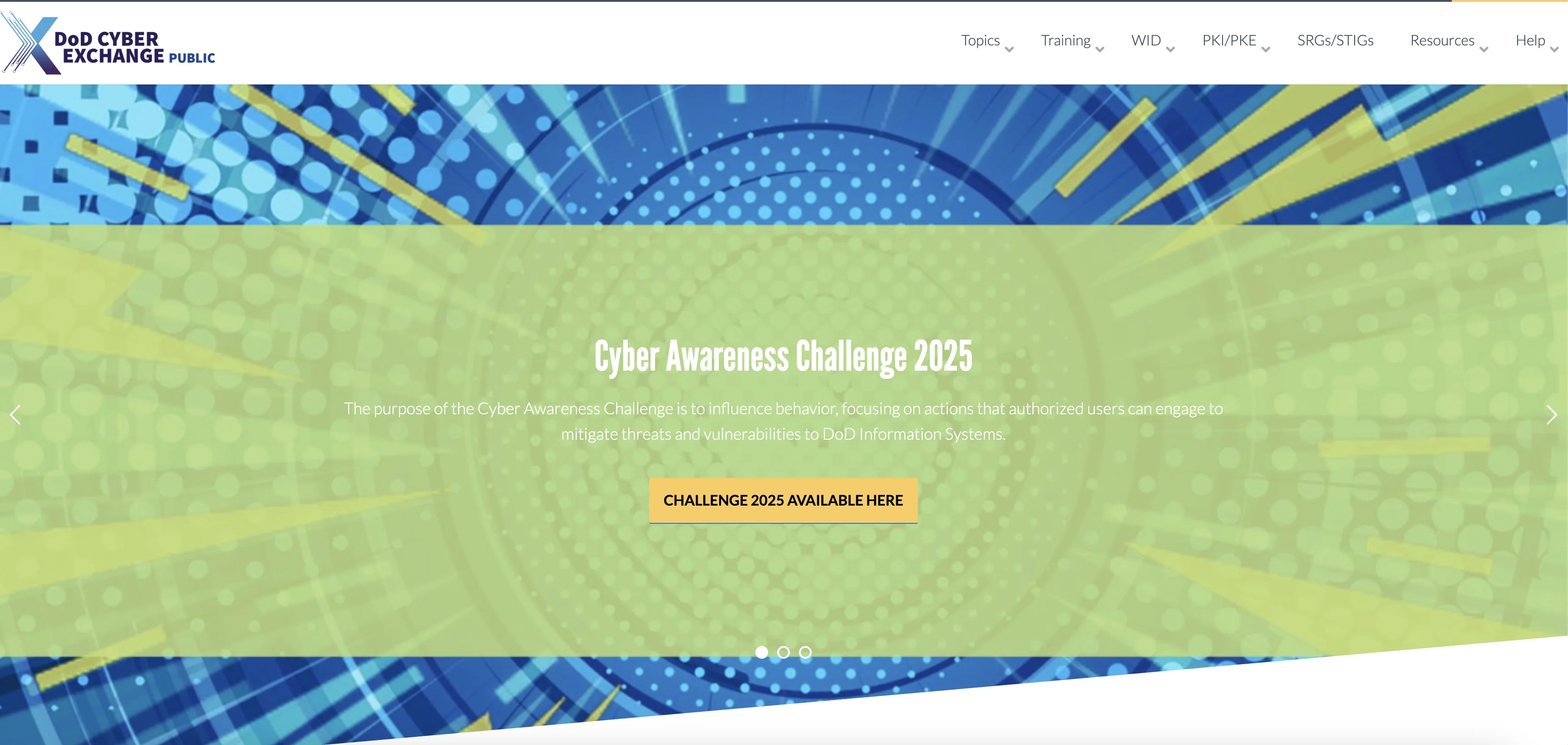
- In the top menu bar (right), select PKI-PKE.
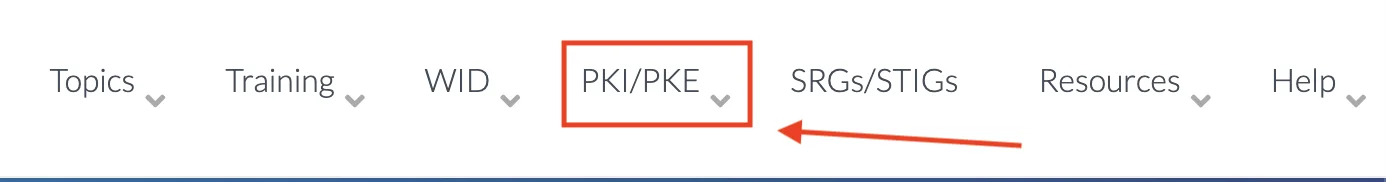

- In the left side menu, click on Document Library.
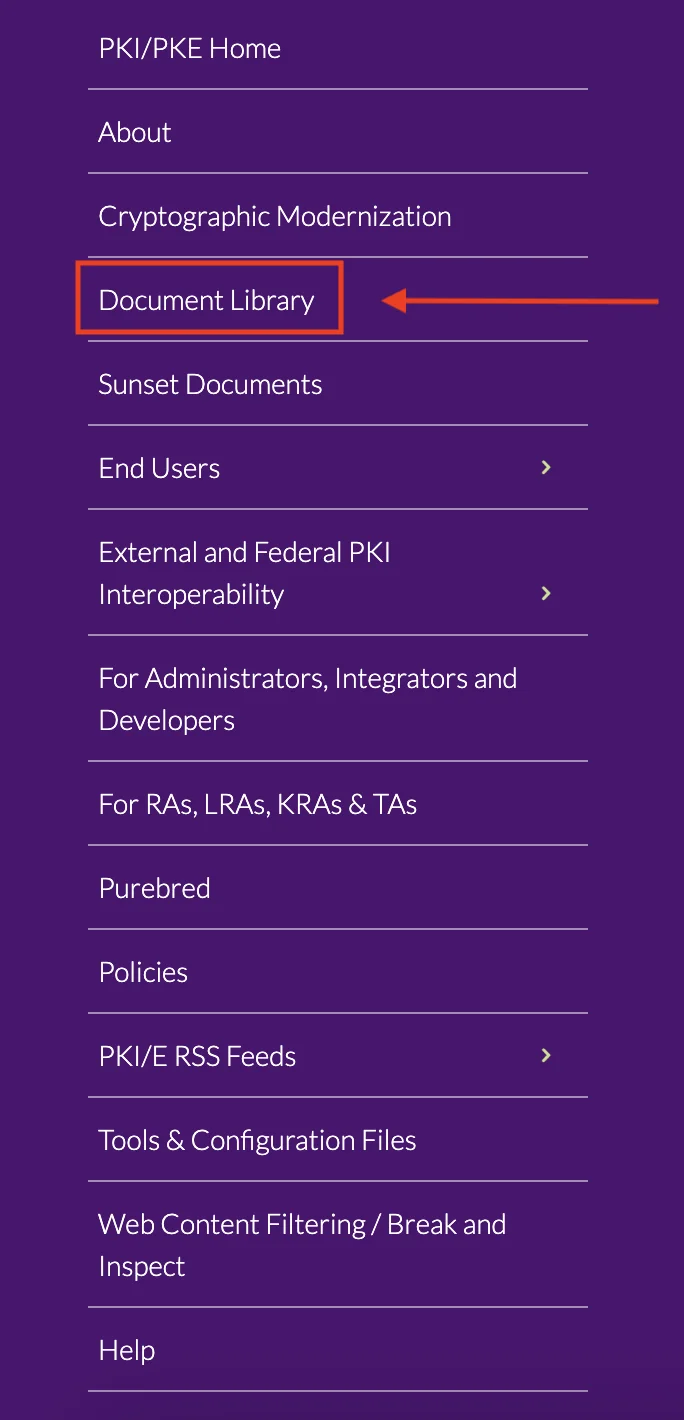
- Search for "DoD Approved External PKI Certificates Trust Chains".
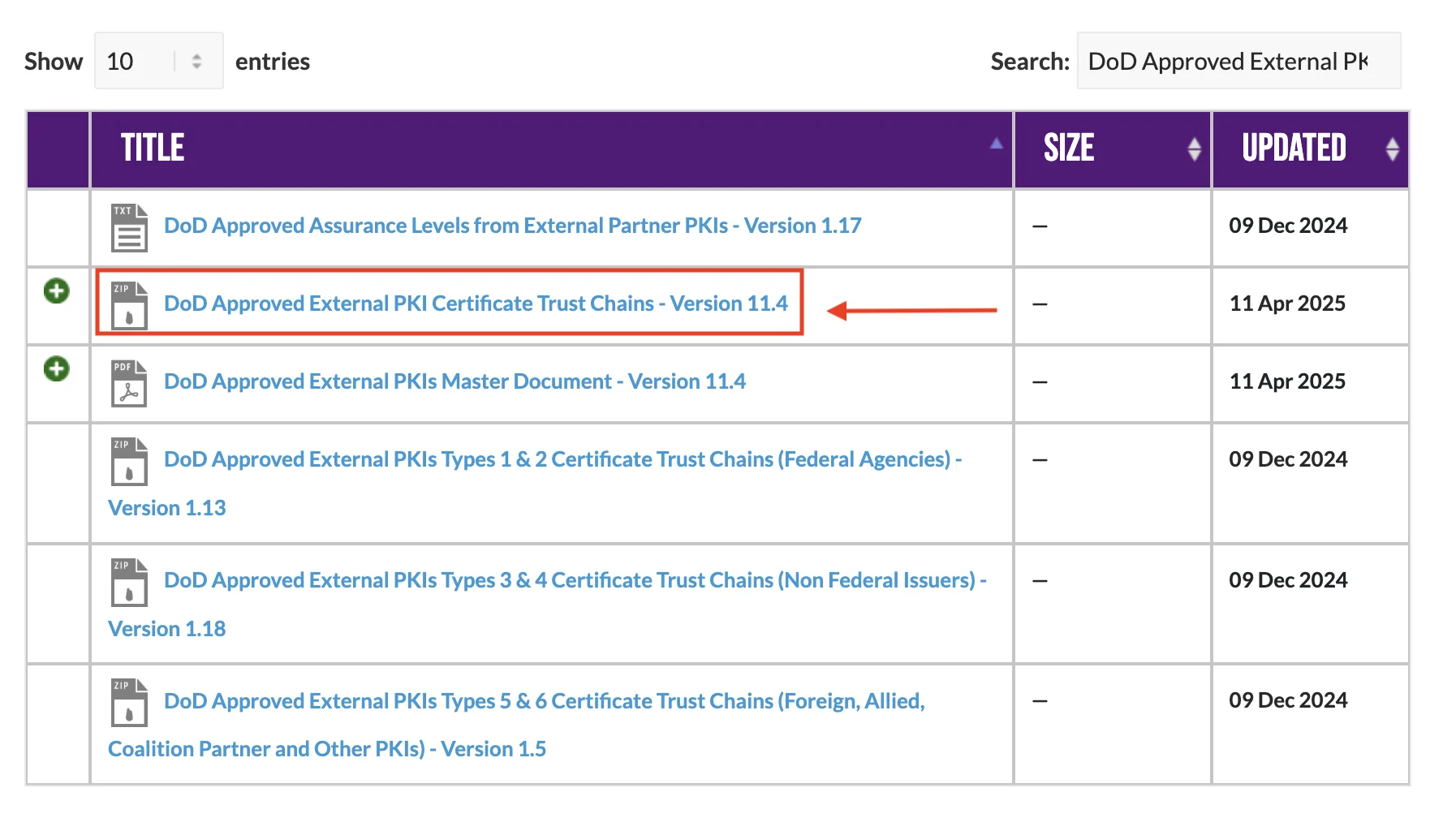
Step 2: Locate, Extract, and Explore the Certificates
- Find the downloaded ZIP file named
DoD_Approved_External_PKIs_Trust_Chains.zip
Where is my downloaded ZIP file?
(Click to expand and see example paths, helpful notes, and images in the tabs below)
(Click to expand and see example paths, helpful notes, and images in the tabs below)
By default, your downloaded file will be saved in your Downloads folder. However, you may have chosen a different location when saving the file—please check your browser's download settings or the location you selected.
- Example Path
- Example Image
/Users/YOURUSERNAME/Downloads/DoD_Approved_External_PKIs_Trust_Chains.zip
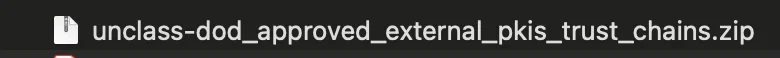
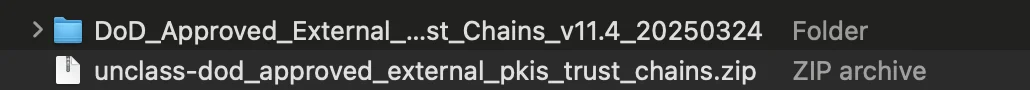
- Double-click the ZIP file to extract it to a folder named
DoD_Approved_External_PKIs_Trust_Chains_vXX.X_YYYYMMDD
Where did it extract?
(Click to expand and see example paths, helpful notes, and images in the tabs below)
(Click to expand and see example paths, helpful notes, and images in the tabs below)
When you extract the zip it will create a folder. By default, the extracted folder will appear in the same location as the ZIP file. If you use a third-party extraction tool or changed the extraction path, the folder may be located elsewhere—check your tool's settings or the location you selected.
- Example Path
- Example Image
/Users/YOURUSERNAME/Downloads/DoD_Approved_External_PKIs_Trust_Chains_vXX.X_YYYYMMDD/
- Open the extracted folder named
DoD_Approved_External_PKIs_Trust_Chains_vXX.X_YYYYMMDD
How to Open?
(Click to expand and see example paths, helpful notes, and images in the tabs below)
(Click to expand and see example paths, helpful notes, and images in the tabs below)
The extracted folder will be named DoD_Approved_External_PKIs_Trust_Chains_vXX.X_YYYYMMDD.
Locate this folder in your downloads (or chosen location) and double-click it to open and view its contents.
- Open the
_DoDfolder inside the extracted folder nameDoD_Approved_External_PKIs_Trust_Chains_vXX.X_YYYYMMDD
Where is the _DoD directory?
(Click to expand and see example paths, helpful notes, and images in the tabs below)
_DoD directory?(Click to expand and see example paths, helpful notes, and images in the tabs below)
The _DoD folder is located within the extracted DoD_Approved_External_PKIs_Trust_Chains_vXX.X_YYYYMMDD directory. Open the extracted folder and look for the _DoD directory as shown below.
- Example Path
- Example Image
/DoD_Approved_External_PKIs_Trust_Chains_vXX.X_YYYYMMDD/_DoD/
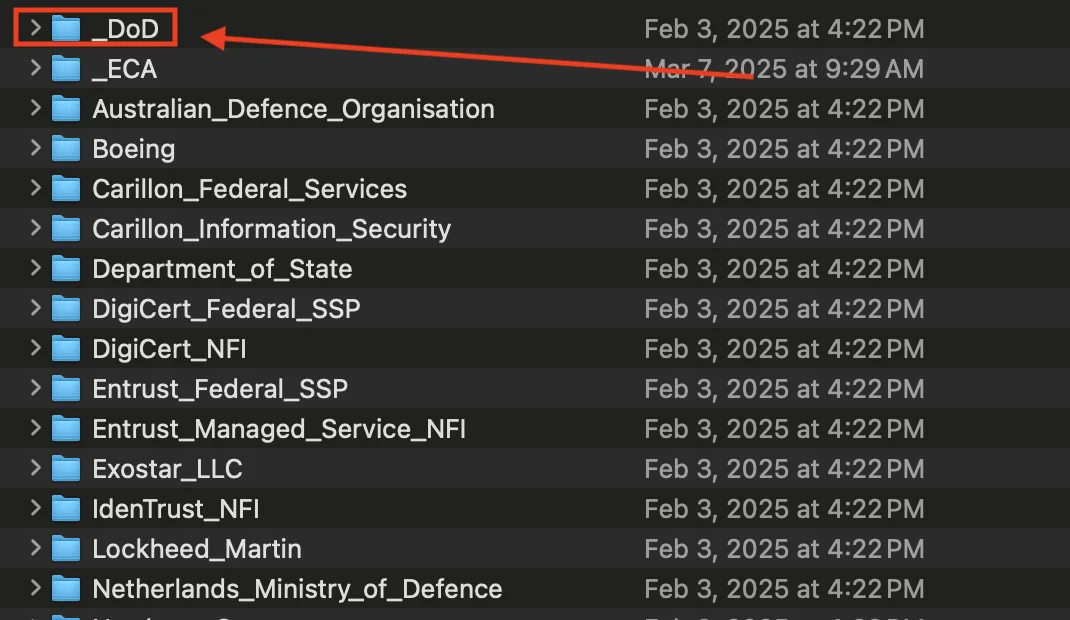
- Find/Verify the folders
Intermediate_and_Issuing_CA_Certs&Trust_Anchors_Self-Signedcontain CA's
Where are the certificate folders?
(Click to expand and see example paths, helpful notes, and images in the tabs below)
(Click to expand and see example paths, helpful notes, and images in the tabs below)
Inside the _DoD folder, you will find:
Intermediate_and_Issuing_CA_Certs(contains Intermediate CA certificates)Trust_Anchors_Self-Signed(contains Root CA certificates)
Each of these folders contains the certificate files (CAs) that you will import into your keychains.
- Example Path
- Example Image DoD
- Example Image Intermediate
- Example Image Root
Intermediate_and_Issuing_CA_Certs Path
/Users/YOURUSERNAME/Downloads/DoD_Approved_External_PKIs_Trust_Chains_v11.4_20250324/_DoD/Intermediate_and_Issuing_CA_Certs
Trust_Anchors_Self-Signed Path
/Users/YOURUSERNAME/Downloads/DoD_Approved_External_PKIs_Trust_Chains_v11.4_20250324/_DoD/Trust_Anchors_Self-Signed
Step 3: Upload Certificates to MDM
- Take the downloaded certificate files (from the extracted folders) and upload them into your MDM according to your MDM provider's documentation.
- Typically, you will create a new certificate payload or profile and add all required Root and Intermediate CA certificates.
- For reference, here are guides for common MDM providers:
Step 4: Configure Configuration Settings (if available)
- Many MDMs allow you to configure trust settings for certificates. For Root CAs, set the trust level to "Always Trust" if your MDM supports it.
- When creating the certificate payload or profile, you may have the option to specify additional keys, such as:
AllowAllAppsAccess– allows all applications to access the certificate.KeyIsExtractable– allows the private key to be exported or extracted (if applicable).
- The specific keys and settings available depend on the certificate payload type and your MDM platform. For detailed information on supported keys and configuration options, see:
- Always consult your MDM provider's documentation for instructions on setting these options and configuring trust.
- After configuration, review the profile for accuracy before deploying.
Step 5: Assign and Deploy the Profile
- Assign the certificate profile to the relevant device groups or users.
- Push the profile to all managed devices.
If a certificate already exists on a device and you deploy it via MDM, the MDM-managed certificate will take control and override any local settings for that certificate. When you remove the certificate profile from MDM, the certificate will be completely removed from the device.
Step 6: Verify on Devices
- On a managed device, open Keychain Access and check the System keychain for the imported certificates.
- Ensure Root CAs are trusted (orange, "Always Trust") and Intermediates are present (blue).
- Test access to DoD resources.
Visual Examples:
Below is a table showing what a properly trusted Root CA certificate and a failed trust setting look like in Keychain Access, as well as the color difference between Root and Intermediate CAs:
| Good (Always Trust) Root CA | Failed Trust Root CA | Root CA (Orange) | Intermediate CA (Blue) |
|---|---|---|---|
 |  |
Troubleshooting Steps
-
Certificates not appearing on devices:
- Ensure the profile was assigned and pushed to the correct devices.
- Check for errors in the MDM deployment logs.
-
Certificates not trusted:
- Verify trust settings in the MDM profile.
- Remove old/expired DoD certificates from devices before deploying new ones.
-
Profile installation fails:
- Check for conflicting profiles or existing certificates.
- Ensure devices are enrolled and communicating with MDM.
-
Access to DoD resources still fails:
- Confirm certificates are in the System keychain and trusted.
- Restart the device and test again.
If a certificate already exists on a device and you deploy it via MDM, the MDM-managed certificate will take control and override any local settings for that certificate. When you remove the certificate profile from MDM, the certificate will be completely removed from the device.
If you found an error, noticed something missing, or need additional help, please submit feedback on GitHub or start a GitHub discussion.
If you'd like to contribute improvements to this guide, feel free to submit a pull request or select edit this page below.