Guide Introduction
This website offers scripts, guides, tools, and helpful links to assist you in setting up CACs, YubiKeys, or IC/ICC Cards for secure authentication on your devices. Whether you're working from a personal or professional device, you'll find resources tailored for both system administrators and end-users.
It is also a place for users to share their own experiences, tips, and solutions—helping give information back to the community and improve the guide for everyone.
This guide focuses primarily on macOS, with some content applicable to Linux or Windows where noted.
Who is this for?
This site is for government employees, contractors, IT administrators, and anyone who uses a CAC, Smart Card, YubiKey, or IC/ICC Card to securely access systems on macOS. If you're trying to get things working—or just make them work better—you’re in the right place.
What are CACs, YubiKeys, IC/ICC Cards and Smart Cards?
Smart Cards is a general term for physical cards with embedded integrated circuits (chips) that can process data. On macOS, Apple refers to CACs, PIV cards, and similar devices (including YubiKeys in smart card mode) as "Smart Cards." These cards are used for secure authentication to computers, web resources, and applications, often providing two-factor authentication and cryptographic security.
A Common Access Card (CAC) is a smart card issued primarily by the U.S. Department of Defense and other government agencies. It is used for secure identification and authentication, enabling access to government computers, networks, and physical facilities. CACs contain embedded microchips that store certificates and cryptographic keys for secure login and digital signatures.
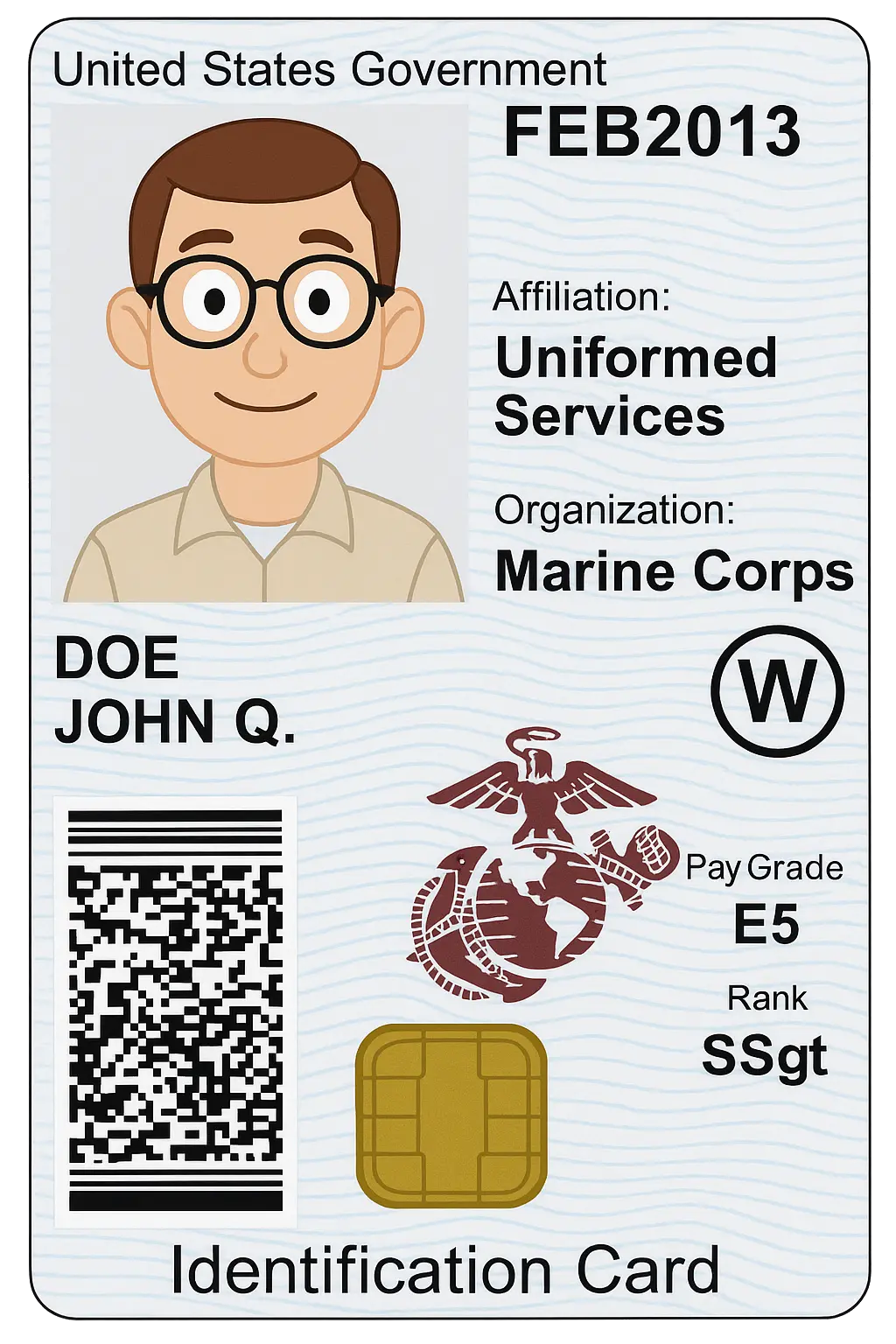
Example of a Common Access Card (CAC)
A YubiKey is a hardware authentication device produced by Yubico. It supports multiple authentication protocols (such as FIDO2, U2F, PIV, and OTP) and can be used as a smart card for secure login, two-factor authentication, and cryptographic operations. Some government agencies allow YubiKeys to be used in place of traditional CACs or PIV cards for secure access.

Example of a YubiKey
IC Cards (Integrated Circuit Cards), also known as ICC Cards, are a broad category of smart cards used across many sectors—including government, banking, healthcare, and corporate environments. These cards store identity credentials, digital certificates, or cryptographic keys, enabling secure login, encryption, and access control.
Unlike CACs and YubiKeys, IC/ICC cards may not follow the DoD's strict standards but still conform to international protocols such as ISO/IEC 7816 or GlobalPlatform. They are widely used in enterprise badge systems, citizen ID cards, EMV banking cards, and secure building access.

Example of a IC Card
All CACs are IC cards, but not all IC cards are CACs. IC/ICC is the broader technical classification.
What are Certificates?
Certificates are digital documents used to prove identity and establish trust between devices, users, and services. They use cryptographic keys to enable secure communication and authentication. Certificates are a core part of how smart cards, IC Cards, CACs, and YubiKeys work for secure login and access.
There are several types of certificates involved in authentication:
-
Root CA Certificate: The top-level certificate in a trust chain, issued by a Certificate Authority (CA) that is trusted by your device or organization. Root CAs can be public (pre-installed on your device) or private (installed by your organization for internal use).

-
Intermediate CA Certificate: Issued by a root CA (or another intermediate CA), these certificates act as a "middle layer" in the trust chain. Intermediate certificates are used to sign user or device certificates, providing an extra layer of security and flexibility. Most certificate chains include one or more intermediate certificates between the root and the end-user certificate.

-
Public CA Certificate: Issued by widely trusted third-party organizations (such as DigiCert, GlobalSign, etc.), these certificates are used to secure public websites and services. Devices and browsers trust these by default.


-
User Certificate: Issued to an individual user and stored on a smart card or security key. This certificate proves your identity when logging in or accessing secure resources. The private key for this certificate never leaves your smart card or device.
User certificates are typically issued by an intermediate CA, but in some cases, they can be issued directly by a root CA (especially in smaller or legacy environments).
These certificates work together in a chain of trust, allowing your device to verify that a certificate presented by a smart card or website is valid and trusted.
What problems does this site solve?
This site is designed to help you get smart cards, CACs, and YubiKeys working smoothly in your environment—whether you’re an end-user or a system administrator, and whether you’re working on a personal device or managing a professional fleet. Here’s how:
-
Providing clear information and guidance
Learn the concepts, requirements, and best practices for using smart cards and certificates on macOS. -
Offering practical commands, scripts, and tools
Access ready-to-use commands and automation scripts to simplify setup, troubleshooting, and ongoing management. -
Solving certificate errors and authentication issues
Understand and resolve common problems with certificates, login failures, and device compatibility. -
Step-by-step setup instructions
Follow detailed guides to configure CACs, Smart Cards, and YubiKeys for your specific needs. -
Troubleshooting for all roles
Find targeted troubleshooting advice for both end-users and IT/system administrators. -
Keeping you up-to-date
Stay current with tested solutions and the latest recommendations for secure authentication.
Learn More & Vendor Links
Apple Resources
📘 Core Deployment Guides
-
Use a Smart Card on Mac Information on using a Smart Card on a MacOS.
-
Introduction to Smart Card Integration Overview of smart card capabilities and use cases in Apple environments.
-
Supported Smart Card Functions on macOS Detailed breakdown of PIV/CAC smart card operations supported across macOS versions.
🔧 Configuration & MDM Settings
-
Configure macOS for Smart Card–Only Authentication Guide to enforcing smart card-only login via system and MDM settings.
-
Advanced Smart Card Options Explains keychain behaviors, cert mapping, certificate trust settings, and policy controls.
-
Certificates Payload (MDM Settings) How to deploy and manage certificate payloads via MDM.
-
Smart Card Payload (MDM Settings) Specific MDM payload options to configure smart card usage on supervised Apple devices.
Government Resources
-
CAC.mil – DoD Common Access Card Portal Official Department of Defense (DoD) site for CAC information, software, and guidance. Managed by the Defense Manpower Data Center (DMDC).
-
IDManagement.gov – FICAM Program Federal Identity, Credential, and Access Management (FICAM) hub, led by GSA. Provides policies, implementation tools, and the Approved Products List (APL) for PIV and smart card hardware/software.
-
DoD Cyber Exchange Central source for DoD cybersecurity tools and policies. Key pages include:
- PKI/PKE Tools
- Access Public Key Infrastructure (PKI) and Public Key Enabling (PKE) documentation, guides, and configuration tools for DoD environments.
- Purebred Derived Credentialing 🔒 CAC login required
- Used to issue and manage secure derived credentials for mobile device authentication.
- PKI/PKE Tools
-
NIST Computer Security Resource Center (CSRC) Publishes federal standards for identity and access. Key documents:
YubiKey Resources
-
Yubico Official Website The manufacturer of YubiKey security keys supporting OTP, FIDO2, PIV, and Smart Card (CAC) standards.
-
YubiKey for Federal Government Solutions tailored for federal agencies, including FIPS-certified YubiKeys and PIV mode usage.
-
YubiKey for State and Local Government YubiKey deployment guidance and solutions for state and local governments.
📚 Additional YubiKey Resources & Tools
- Yubico PIV Tool (GitHub) — Open-source tool for managing YubiKey PIV functionality
- Phishing-Resistant MFA Deployment Best Practices (Federal)
- YubiKey Compatibility with macOS
- YubiKey for macOS Login Guide
- YubiKey Manager for macOS (Download)
If you found an error, noticed something missing, or need additional help, please submit feedback on GitHub or start a GitHub discussion.
If you'd like to contribute improvements to this guide, feel free to submit a pull request or select edit this page below.